NoClone will quickly identify and delete duplicate files that could be hogging precious hard drive space.
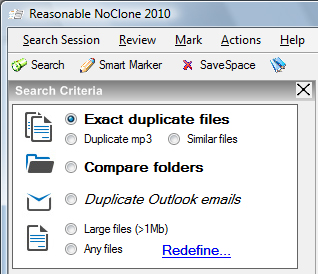
The program offers several search options. It can locate files that are exactly the same, or files that are similar: images with very minor edits, for instance, or MP3 files with different metadata. You can also search for duplicate MP3 files by tags alone, which isn't an entirely precise method but is at least very fast. And NoClone can even scan your Microsoft Outlook folders, locating and highlighting duplicate emails.
Once the search is complete then NoClone displays a report, listing all the duplicates it's discovered. You get to choose which ones to keep, and which, if any, to remove. (Duplicate files are sometimes a necessity - DLLs in application folders, for instance - so don't wipe anything unless you're entirely sure that's safe.) And then you may delete any selected files in a click.
Please note, this free edition of the program has significant limitations. In particular, it will scan a maximum of 3 network drives and 100,000 files in one session. To remove both restrictions you'll need to purchase NoClone Enterprise, which is yours for $29.90
Verdict:
NoClone offers plenty of search flexibility, but the 300,000 file limit could be a problem and the Enterprise version is a little expensive








Your Comments & Opinion
Free up valuable hard drive space by locating and deleting duplicate files
Easily run complex desktop searches with this powerful, portable tool
Free up valuable hard drive space and speed up your PC with this useful optimisation tool
Discover exactly how your hard drive space is being used with this powerful analytical tool
An easy-to-use hard drive cleanup tool
Preserve your desktop icon layout with this handy backup tool
Preserve your desktop icon layout with this handy backup tool
Take control of your file and folder management with this powerful – if slightly unrefined - utility
Take control of your file and folder management with this powerful – if slightly unrefined - utility
Convert almost any documents to PDF format in a click